Frequently asked questions about “BadSuccessor,” a zero-day privilege escalation vulnerability in Active Directory domains with at least one Windows Server 2025 domain controller.
Background
Tenable’s Research Special Operations (RSO) and the Identity Content team has compiled this blog to answer Frequently Asked Questions (FAQ) regarding a newly disclosed zero-day in Active Directory called BadSuccessor.
FAQ
What is BadSuccessor? BadSuccessor is the name of a zero-day privilege escalation vulnerability in Active Directory that was discovered and disclosed by Yuval Gordon, a security researcher at Akamai. According to Gordon, the flaw exists in delegated Managed Service Accounts (dMSAs), a service account type in Active Directory (AD) that was introduced in Windows Server 2025 to enable the migration of non-managed service accounts. What are the vulnerabilities associated with BadSuccessor? As of June 2, Microsoft had not assigned a CVE identifier for BadSuccessor. Microsoft is the CVE Numbering Authority (CNA) for its products. Since there are currently no patches available for BadSuccessor, no CVE has been assigned. If Microsoft does assign a CVE alongside patches for it, we will update this blog accordingly. How is BadSuccessor exploited? To exploit BadSuccessor, an attacker needs to be able to access a user account with specific permissions in AD, and at least one domain controller in the domain needs to be running Windows Server 2025. Based on Akamai’s research, even if an AD domain is not using dMSAs, nor operates at the 2025 functional level, all that is required is that a targeted user has either the permission to: Create a new dMSA (msDS-DelegatedManagedServiceAccount object class) in any container or organizational unit (OU) Abuse an existing dMSA by modifying its msDS-ManagedAccountPrecededByLink attribute When was BadSuccessor first disclosed? On May 21, Akamai published a blog post about BadSuccessor, which included a detailed overview of the flaw, as well as detection and mitigation guidance. How severe is BadSuccessor? BadSuccessor has the potential to be very severe, as exploitation could allow an attacker to achieve full domain, and then forest, compromise in an Active Directory environment. However, one mitigating factor is that it only affects domains with at least one Windows Server 2025 domain controller. How prevalent are AD domains with at least one Windows Server 2025 domain controller? Based on a subset of Tenable’s telemetry data, we found just 0.7% of AD domains have at least one Windows Server 2025 domain controller. This appears to be lower than other statistics we’ve seen reported. Was BadSuccessor exploited as a zero-day? As of June 2, there have been no indications that BadSuccessor has been exploited in the wild. Why is it called BadSuccessor? According to Gordon, the name “BadSuccessor” is tied to the fact that the user account (or dMSA) becomes the nefarious “successor” by inheriting the elevated privileges of another identity in the AD environment.
6/ We named this attack BadSuccessor, because that’s exactly what the dMSA becomes – the unintended heir to a high-privilege identity.
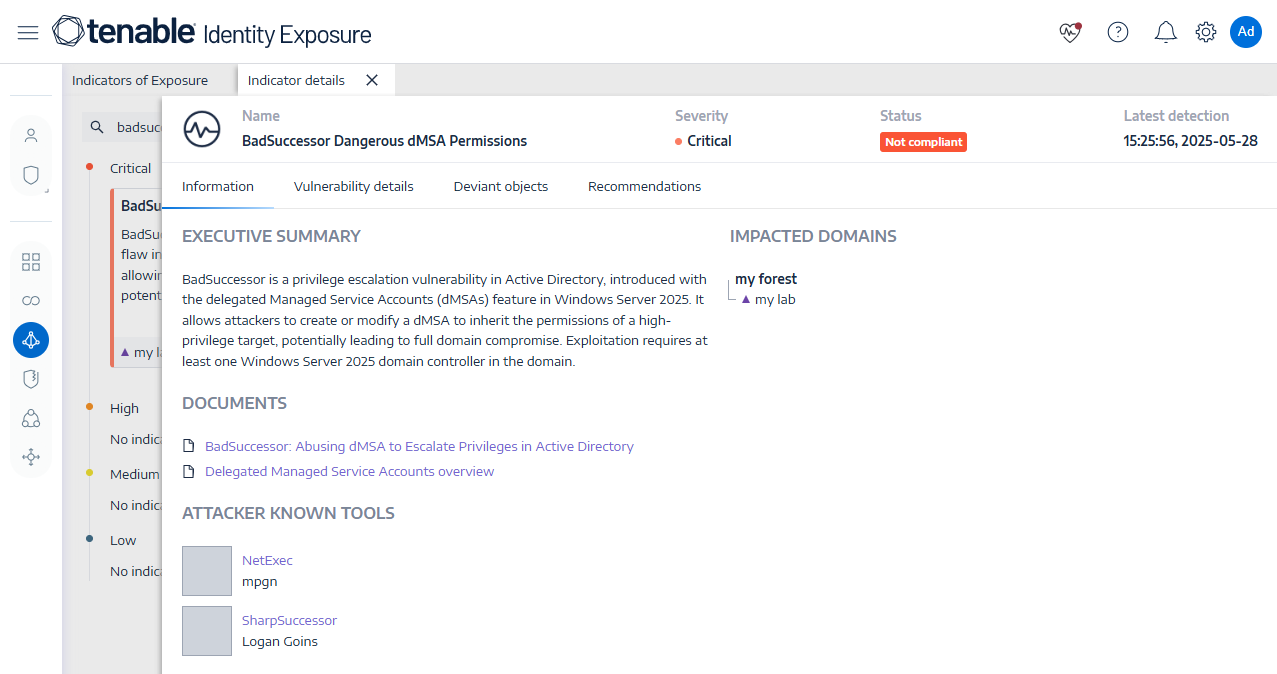
A successor, with all the right keys., Yuval Gordon (@YuG0rd) May 21, 2025 Is there a proof-of-concept (PoC) available for BadSuccessor? Yes, there are several proofs-of-concept (PoCs) for BadSuccessor available on GitHub, including a.NET implementation called SharpSuccessor. It is also available in NetExec, the successor to the infamous CrackMapExec hack tool. It was also added to BloodyAD, the Active Directory privilege escalation framework. Are patches or mitigations available for BadSuccessor? As of June 2, there were no patches available for BadSuccessor. However, in the Akamai blog post from May 21, Microsoft indicated they would “fix this issue in the future.” If and when a patch becomes available, we will update this section. Akamai’s blog post includes details on detecting BadSuccessor as well as mitigation suggestions. Has Tenable released any product coverage for these vulnerabilities? While Microsoft has not yet released patches for BadSuccessor, Tenable Identity Exposure customers can utilize our recently released (v3.95) Indicator of Exposure (IoE) for BadSuccessor.Once Microsoft assigns a CVE and releases patches, we will update this section with additional Tenable coverage.
Get more information
BadSuccessor: Abusing dMSA to Escalate Privileges in Active Directory Join Tenable’s Research Special Operations (RSO) Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
First seen on securityboulevard.com
Jump to article: securityboulevard.com/2025/06/frequently-asked-questions-about-badsuccessor/
![]()